Jonathan Griffith, Product Manager, Industrial Communications & Power Supplies at AutomationDirect, wrote an article for Machine Design April 2018 titled What’s the Difference Between Traditional and Hosted VPNs?
Griffith points out that connecting programmable logic controllers (PLCs), human machine interfaces (HMIs) and other automation system components to the industrial internet of things (IIoT) for remote access is important for many manufacturing plants, and to the machine builders providing equipment and services to these plants. In the past, remote access was often accomplished via a router without a virtual private network (VPN), but these router-only connections to the Internet should not be implemented today due to security risks.
Instead, a VPN should be used, as it is one of the key elements to a defense-in-depth strategy. However, implementing a secure IIoT connection to automation system components via a VPN often presents cost, technical and resource allocation issues.
The two solutions presented in his article address these challenges, but in different ways. Each solution has its own advantages and design considerations as noted in the Table. The two options are hosted VPN and traditional VPN.
Table: IIoT Connection Considerations: Hosted VPN vs Traditional VPN
| Hosted VPN | Traditional VPN | |
| External Cost | ||
| Initial | Medium | High |
| Sustaining | Bandwidth dependent | Low |
| Internal Support Cost | Low | High |
| Required Technical Expertise | Low | High |
| Changes to Existing Firewall | Not required | Required |
| Security Risk | Low | Low |
| Data Dashboards | Available through subscription | Typically not available |
| Data Storage & Access | Available through subscription | Typically not available |
Hosted VPN Solution
A hosted VPN solution provides secure IIoT connectivity with simple setup and network configuration. These solutions usually include a local VPN router, a cloud-hosted VPN server and a remote VPN client. Automation system components are connected locally to the VPN router, which connects to the cloud server. The VPN client connects by laptop or PC to the cloud, and ultimately to the local automation system components.
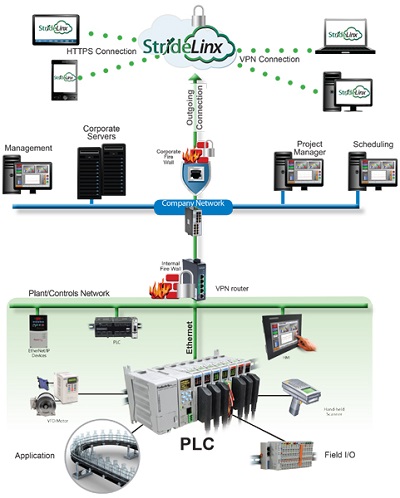
To accomplish this, the local VPN router makes a VPN connection to the cloud server immediately upon startup, but the VPN client only connects upon a verified request from the remote user. Once both connections have been made, all data passing through this VPN tunnel is secure.
Griffith says hosted VPN solutions only require simple router configuration because the router is connected to a predefined cloud server.

This allows the hosted VPN vendor to deliver the router preconfigured, so the user only needs to add basic network information. The router’s default firewall settings keep the plant floor network separate from the corporate network.
By only providing the functionality needed for IIoT connectivity, this AutomationDirect StrideLinx VPN router, installed on the far right of the DIN rail and connected to the PLC, simplifies implementation and use.
Security risk is minimal with this solution because the remote client connection to the cloud server uses the robust encryption standard SSL/TLS. What’s more, Griffith says, A typical hosted VPN solution has a free monthly bandwidth allocation for basic operation, and then offers a premium plan for additional bandwidth.
Traditional VPN Solution
A traditional VPN solution requires a third-party HMI, either PC-based or embedded, to provide data logging and widgets for configuring remote access screens.
With hosted VPN solutions, users can configure dashboards using widgets for remote access via their PC or mobile device. Users can also configure alerts and notifications to indicate when parameters fall outside a predefined range.

Creating remote access viewing screens can be cumbersome if this feature is not provided, so this must be taken into account when evaluating competing hosted VPN solutions.
A hosted VPN solution uses a local VPN router to connect through the internet, with a secure VPN tunnel to a second remote VPN router, or to a software client, which is typically installed on a PC.
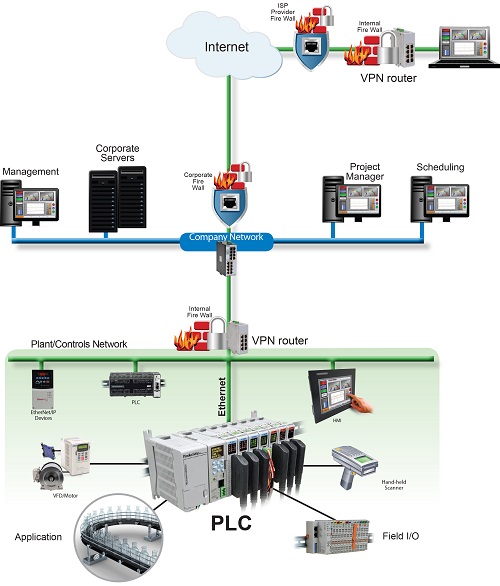
This solution was the only method of secure two-way access prior to the fairly recent introduction of cloud-based remote access solutions via a hosted VPN around 2012, so it’s widely used. But the IT team must have the capability and willingness to support this solution at both the local and remote sites for each installation.
When implementing an IIoT solution for remote access, a VPN is necessary to provide the required security. Older solutions without a VPN simply don’t provide the needed level of protection from intrusion.
Griffith concludes:
Once the decision has been made to use a VPN for remote IIoT access, the two main types of solutions are a hosted VPN and a traditional VPN. The hosted VPN is the more modern solution and works well in most instances. The traditional VPN provides the utmost in performance for implementations requiring very high bandwidth, but is more complex to design, install and support.
To read more articles about communications, click here.

