Cloud technologies enable remote connectivity for industrial applications, but can introduce issues unless built from the ground up with cybersecurity in mind.
Jonathan Griffith, product manager for Industrial Communications & Power Supplies at AutomationDirect, wrote an article for the November 2019 issue of Control Engineering titled Secure Remote Connections with Cloud Technologies. Here’s a summary, click on the link above for the full text.
Today’s end users at industrial plants and facilities expect and demand digital access to almost anything technology-based, often remotely through mobile devices. Industrial control applications, on the other hand, are often isolated, and remote access options have lagged consumer applications. Cybersecurity is a key concern, but careful attention to the hardware, software, and networking systems can enable secure remote connections.
A Solid Cloud Foundation
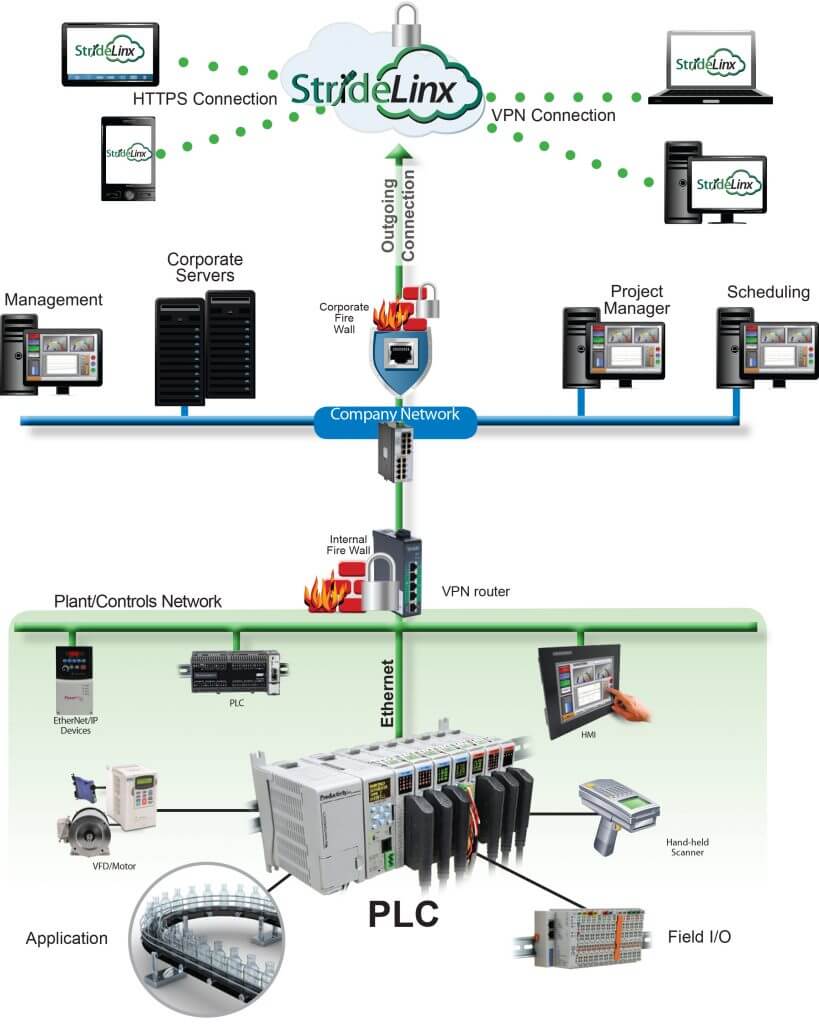
Personnel with a strong information technology (IT) skillset can create and maintain connectivity solutions to plant floor operations technology (OT) systems, usually by creating and maintaining virtual private networks (VPNs). VPNs can provide satisfactory performance but are difficult to set up and maintain. For these reasons, many users are turning to established cloud-based solutions, specialized for industrial remote connectivity, offering the necessary security, along with other benefits.
Distributed Resources
Compared to basic VPNs, a cloud-based solution can provide improved availability because it uses many servers and data centers. These types of modern computing architectures are scalable, with provisions to work securely with internet of things (IoT) applications using popular protocols like MQTT. Industrial cloud solutions are also natively suitable for handling the three main types of databases:
- Relational: Such as configuration information
- Non-relational: Such as events, alarms, and logs
- Time series: Such as continually arriving timestamped analog process data.
Five Cybersecurity Issues to Address
Cybersecurity is a complex topic, and many end users are concerned with creating their own cyber-secure remote connectivity solution. Best practice for any provider of such solutions would include adherence to a comprehensive information security management system (ISMS) following the ISO 27001 standard, confirmed by third-party audits. The top five issues are:
- Encrypted connections
- Centralized monitoring, logging, and analysis
- Vulnerability management
- Access control
- Software development life cycle
On-Premises Security
Most OT technologies were not designed with security in mind. Therefore, a fundamental need is to ensure the machine local area network (LAN) is isolated from the wide area network (WAN), typically by using a firewall router blocking all inbound WAN-to-LAN traffic unless specifically enabled. However, trusted outbound LAN-to-WAN traffic is generally allowable, and is the preferred way for OT systems to integrate with IT cloud platforms without requiring more complex solutions.

Browser and App Security
Even when a cloud-based remote connectivity solution is secure, the associated browser-based or mobile-based applications can be targets of attack.
As most users know from their personal email, banking and other computer-based accounts, login security is paramount. In addition to a unique and long password, users should consider using systems that allow two-factor authentication (2FA) as an additional layer of protection. Most often, users open another authenticator app on their mobile device to obtain a one-time passcode as they log in.
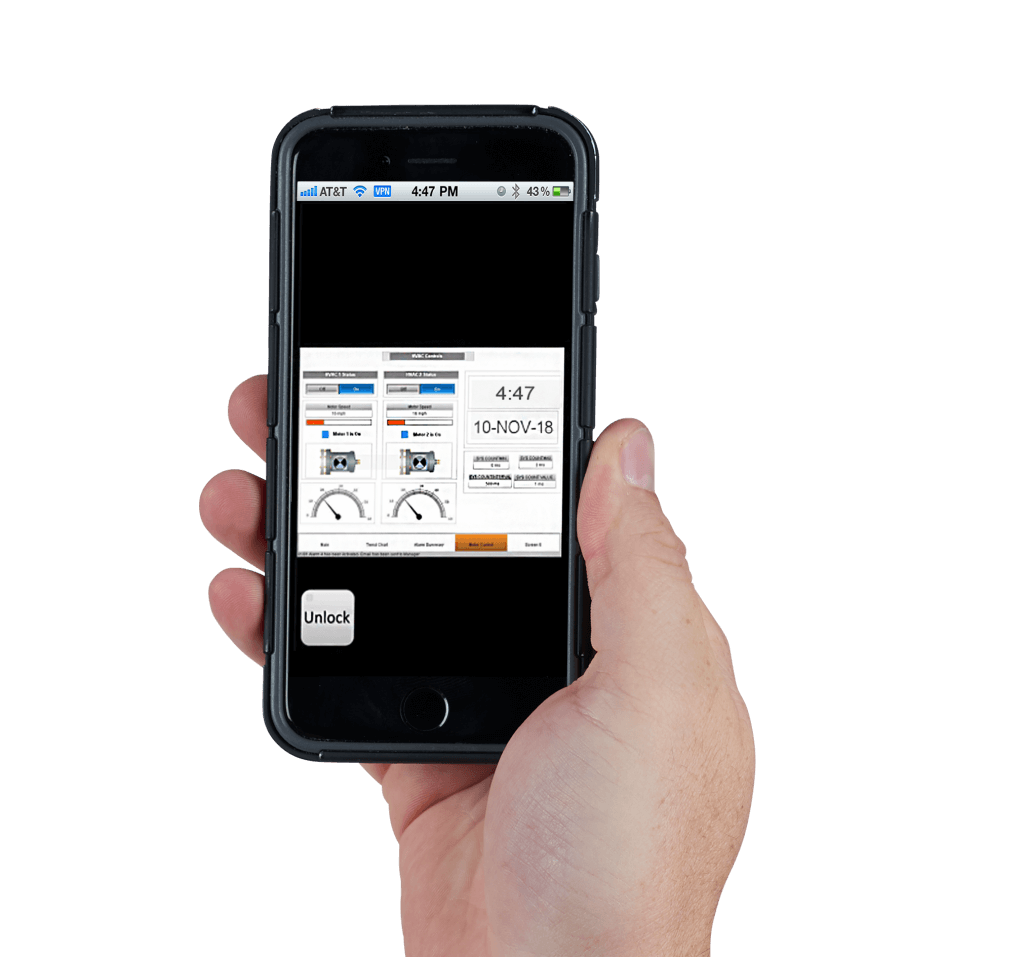
Best practice is for administrators to carefully assign users the minimum privilege necessary for performing their tasks. When mobile apps are available, they can be more convenient than web access because they are easier to use and are tailored for a specific role.
Confident Cloud Connections
Remote monitoring and control, especially via mobile devices, is considered a must-have feature for many industrial automation users. It may be possible for some users to develop their own connectivity software, but the cybersecurity risk is significant and demands extensive effort for ongoing maintenance and mitigation.
Cloud platforms offer better technical solutions, follow the latest industry security standards, are continually audited, and offer mobile apps to help end users get running quickly, with minimal maintenance required throughout the lifecycle.

