Protecting control systems from bad actors requires a holistic approach that includes technology, standards, and most importantly, a “never trust, always verify” attitude.
By Tim Wheeler, Cybersecurity Manager, Automation Direct
Industrial enterprises worldwide face ever greater numbers of cyberthreats, especially from malware and ransomware. According to global data and business intelligence platform Statista, last year, across 10 major industries, the manufacturing sector experienced the largest share of cyberattacks globally at more than 25%.
With that kind of pressure, those in charge of cybersecurity for manufacturing operations should consider implementing a zero-trust security architecture. It features strict access controls, trusts no one inside or outside a facility’s physical and network perimeters, and validates every stage of digital interactions, from core plant operations to the edge to the cloud.
But ensuring the zero-trust approach works requires an understanding of the threats, the potential operational vulnerabilities, and the resources available to help.
Threats Growing Relentlessly
As anyone familiar with operational technology (OT) knows, security threats of all types are growing in both sophistication and frequency. Common vectors for industrial cyber attacks often exploit vulnerabilities in web applications, such as SQL injection, arbitrary file upload, and remote command execution. These avenues can enable attackers to bypass many security measures and gain unauthorized access to industrial networks.
Another vector is the corporate enterprise network. With the integration of both information technology (IT) and OT networks, attackers who succeed in penetrating the former can gain subsequent access to the latter — including the industrial control systems (ICSs) and supervisory control and data acquisition (SCADA) systems.
At the same time, generative artificial intelligence (GenAI) offers hackers new ways to penetrate security defenses via social engineering and deepfake impersonations that can deceive employees into compromising security protocols. GenAI also can accelerate the development pace of malicious code for exploits by malware while expanding its reach and amplifying its impact.
NIST Debuts Cybersecurity Framework 2.0
This evolving threat landscape is the main reason that, last February, the U.S. National Institute of Standards and Technology (NIST) unveiled its Cybersecurity Framework (CSF) 2.0. It’s a comprehensive guide aimed at reducing cybersecurity risks by advising all kinds of organizations — beyond the NIST CSF 1.0’s focus on critical infrastructure — on best practices to safeguard their networks, data, and operations.
While CSF 2.0 offers a wealth of resources to aid in establishing these cyber safeguards, NIST also offers a 299-page specialized guide for OT security, NIST SP 800-82r3, released in September 2023. In addition, an industrial-grade security approach should also consider adhering to the ISA/IEC 62443 series of standards. These, too, provide security best practices as well as methods to assess security performance levels.
Even more, ISA/IEC 62443 offers ways to bridge two critical gaps that often occur in industrial cyber security models. One is the widespread gulf that commonly exists within industrial enterprises between OT and IT domains; the other is the tradeoffs that must be weighed in implementing adequate security measures without compromising process performance and safety with undue latencies.
Prioritizing Life Safety and Deterministic Controls of Industrial Systems
Enterprise cybersecurity experts face significant challenges in protecting IT networks from threats. After all, these networks link users with email, web collaboration tools, and voice communications, plus provide access to company databases, customer relationship management (CRM) systems, and more. Malware, data breaches, and damaged data or devices can hinder user productivity and impact a company’s ability to conduct transactions.
But if an enterprise IT network is breached, the odds are almost 100% that no one is ever injured or worse.That’s not the case with OT networks. In these settings, a breach by hackers — be it from a disgruntled current or former employee, malicious individuals, or even sovereign state actors — can interfere with critical operations or safety measures, potentially causing severe or even fatal injuries.
Modern industrial network security faces unique challenges that distinguish it significantly from non-industrial networks, as outlined in theNIST information resources.
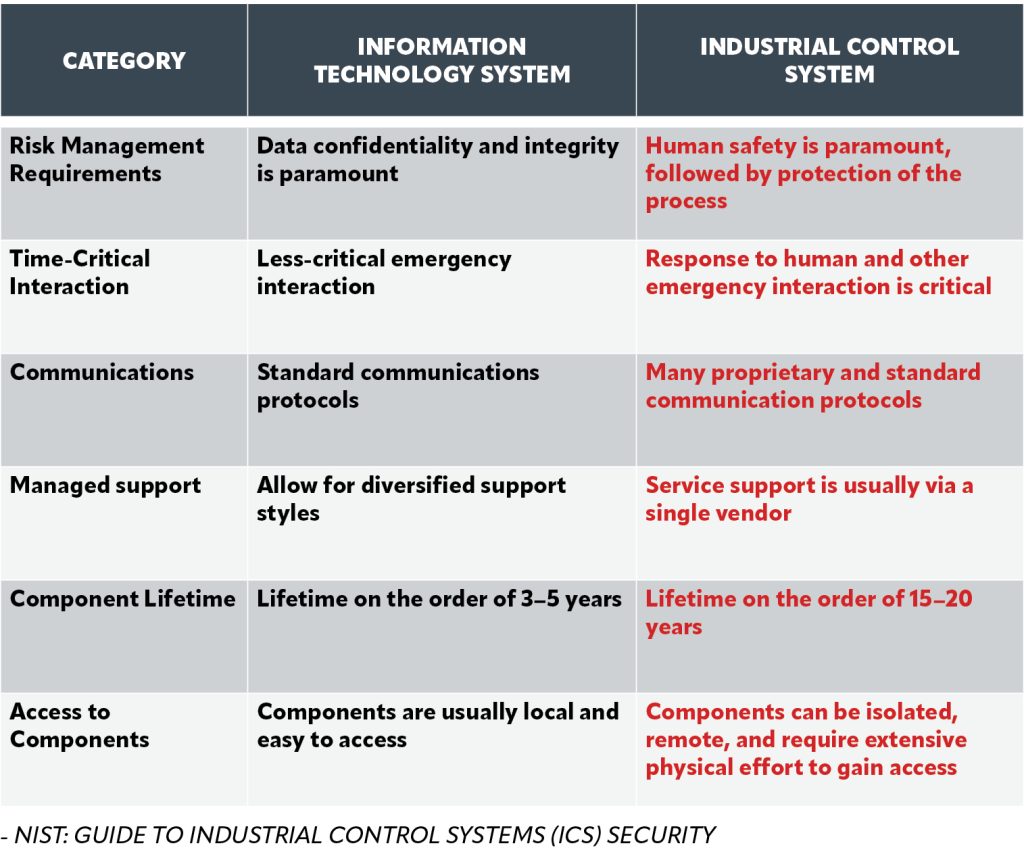
Another big differentiating factor in OT networks is the need for precise, deterministic timing of the operational data running through them. The automation and control components of ICS systems typically require continuous operation and real-time or near-real-time actuator responses. They also must have extremely high reliability (99.9% uptime or better, and even more in critical communication networks).
In contrast, enterprise IT networks generally operate on a best-effort basis and are primarily needed during business hours. And, unlike traditional IT systems, OT systems often operate in harsh and remote environments, rely on legacy technologies, and have long lifecycles. These factors can make it difficult to implement and maintain cybersecurity controls. As a result, the potential consequences of a security breach in an industrial setting are considerably higher than in a typical enterprise IT environment.
Finally, ICS and SCADA systems are inherently networked. And because, more and more, they connect with enterprise IT networks, they’re exposed to the vulnerabilities in the latter that hackers can exploit. In addition, remote-operated wireless SCADA systems, which can use public IP addresses and various wireless communications media, such as cellular, radio, satellite, and microwave, can be especially susceptible to cyberattacks.
Why OT Threats Keep Growing
Influenced by various factors (explained below), the vulnerabilities of OT networks and the ICS and SCADA systems are impacted by new security technologies, policies, and procedures implemented to defend against attacks.
OT networks and systems prioritize stability and real-time speeds, so protecting them requires a cautious approach that includes testing new technologies before implementation. Absent clearly defined policies and procedures — combined with inadequate monitoring and intrusion detection systems – can exacerbate risks, leaving OT devices susceptible to exploitation and unauthorized access.
In navigating these challenges, it’s crucial to recognize that there are no perfect solutions — only trade-offs. Consequently, OT professionals often find themselves playing catch-up with potential risks in the current landscape.
For example, while adopting higher levels of encryption could potentially enhance cyber protections, implementing such encryption may significantly impact system reaction times, adding delays ranging from 100 milliseconds to a full second in responding to real-world inputs. These delays can introduce critical latencies that can undermine production performance and even plant safety.
As the manufacturing sector moves toward digital transformation of industrial automation and control systems, it opens the door to more cybersecurity vulnerabilities.. Primary among them:
- Remote access for workers and vendors. The increasing mobility of workers has led to greater demands for 24×7 remote network access for engineering, operations, and technical support personnel, sometimes leading to less secure network connections and security practices.
Concurrently, more and more OEM suppliers want to provide remote monitoring of their equipment, with some even wanting to provide their machines’ operations as a subscription service. Either way, giving OEMs network access can provide hackers a back door to a plant’s OT infrastructure if an OEM’s safeguards are compromised.
In many OT environments, remote access has been implemented in haphazard ways by editing a firewall’s rules to make “wide” tunnels through them. Then these modifications are not regularly audited and monitored. External access authentication of these should be time-bound and require regular revalidation.
- OT device vulnerabilities. While OT devices are integral to plant processes, they face cybersecurity risks of their own. Malware can damage them or disrupt their operation, while human errors, such as poor configurations or falling for phishing scams, can compromise them. In addition, outdated software lacking current security updates and inadequate monitoring can leave systems exposed.
Another vulnerability of OT devices can originate from the sluggish integration of new technologies and the absence of well-defined policies and procedures. This delay in adopting advancements is compounded by slow reaction times, hindering the implementation of necessary security measures. Furthermore, inadequate monitoring and intrusion detection systems worsens the situation, leaving OT devices vulnerable to exploitation and unauthorized access.
- Growing use and integration of commercial and open source technologies. Hackers can exploit the various and always-changing vulnerabilities of Windows and Linux operating systems, SQL databases, and Ethernet protocols to insert disruptive malware. Spyware can also secretly introduce advanced persistent threats, keystroke recorders, and data exfiltration agents to conduct industrial espionage and steal intellectual property.
- Proliferation of “how-to” documentation and actual code on the Internet. This information is readily available on the so-called Dark Web and has lowered the bar for the technical competencies needed to hack industrial control systems. GenAI has made it even easier for threat actors to code malware. It’s also possible to subscribe to malware-as-a-service.
- Integration of a company’s legacy plant systems with its enterprise systems. Interconnecting OT and IT networks exposes the former to the latter’s vulnerabilities. It also introduces ambiguity within organizations as to which group — enterprise IT or process engineering — owns responsibility for overall cyber security.
At the same time, increasing external connectivity,such as the Industrial Internet of Things (IIoT), expands the threat surface even more. While many companies are implementing edge and cloud technologies into their OT landscapes, some may assume the security of their cloud providers covers their own data and applications. But often that is not the case unless they pay for managed security services.
OT Cyber Security Overview
Simply put, effective OT cyber security requires collaboration between IT and OT teams, risk management, compliance with industry standards and regulations, and, importantly, regular training not only of OT personnel but all employees, including executive management.
As previously mentioned, an overall zero-trust security architecture is recommended. It should cover not only ICS and SCADA systems on plant floors but also systems managing building automation, physical access, and safety. External connectivity must be carefully managed with a zero-trust approach, too. To implement this architecture, organizations must mount a concerted, well-resourced effort — supported by plant and executive management — to do the following:
- Understand the unique risks and challenges of OT systems and supporting infrastructure.
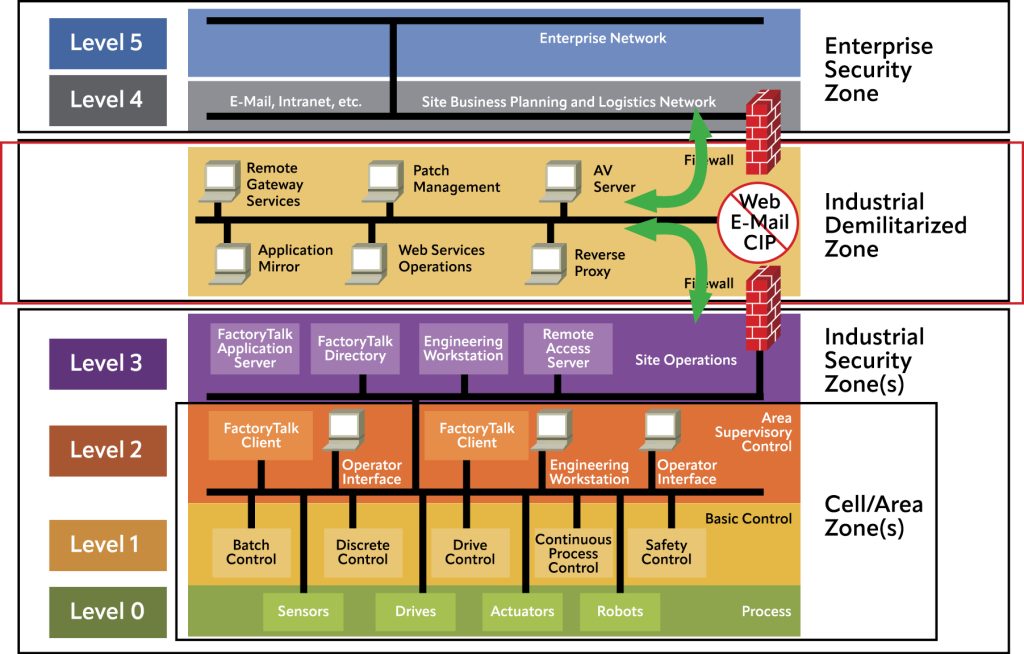
- Identify and inventory OT assets at every plant operating level, using the Purdue Model
- Assess cybersecurity risks at every one of those levels.
- Develop and implement cybersecurity policies and procedures — and, importantly, governance.
- Implement security controls not just on OT devices and systems but also supporting infrastructure.
- Implement continuous monitoring and rapid incident response protocols.
- Engage in threat intelligence and ensure safeguards can stop the latest ones.
- Provide security awareness training and ongoing communications throughout the organization.
- Review at least yearly, if not semiannually, all security controls, risks, monitoring, incident response protocols for changes in the OT landscape (for example, new systems, upgraded legacy systems, new external connectivity privileges, and more), new threats, and new personnel.
AutomationDirect, your partner in cybersecurity
Even with the comprehensive guidance from NIST’s Cybersecurity Framework (CSF) 2.0 and SP 800-82r3 and the ISA/IEC 62443 series of standards, implementing a zero-trust architecture for an OT environment can be a tall order. To complement these guidelines and standards, Automation Direct invites readers to visit its online cybersecurity library of solid information advising how to get started with cyber safeguards, best practices, security advisories, and more. Future editions of Automation Notebook will feature highlights to inform and educate readers on these topics.

