Contemporary industrial cybersecurity measures require the right hardware and software technologies, but must also incorporate user best practices.
Damon Purvis, PLC Product Manager at AutomationDirect, wrote an article which posted to the January 2022 publications Control Engineering and Industrial Cybersecurity Pulse. The article is titled Cybersecurity-Centered Systems and Fundamentals (also found at Cybersecurity-Centered Systems and Fundamentals ) and it describes how modern industrial system cybersecurity involves both technologies and user best practices.
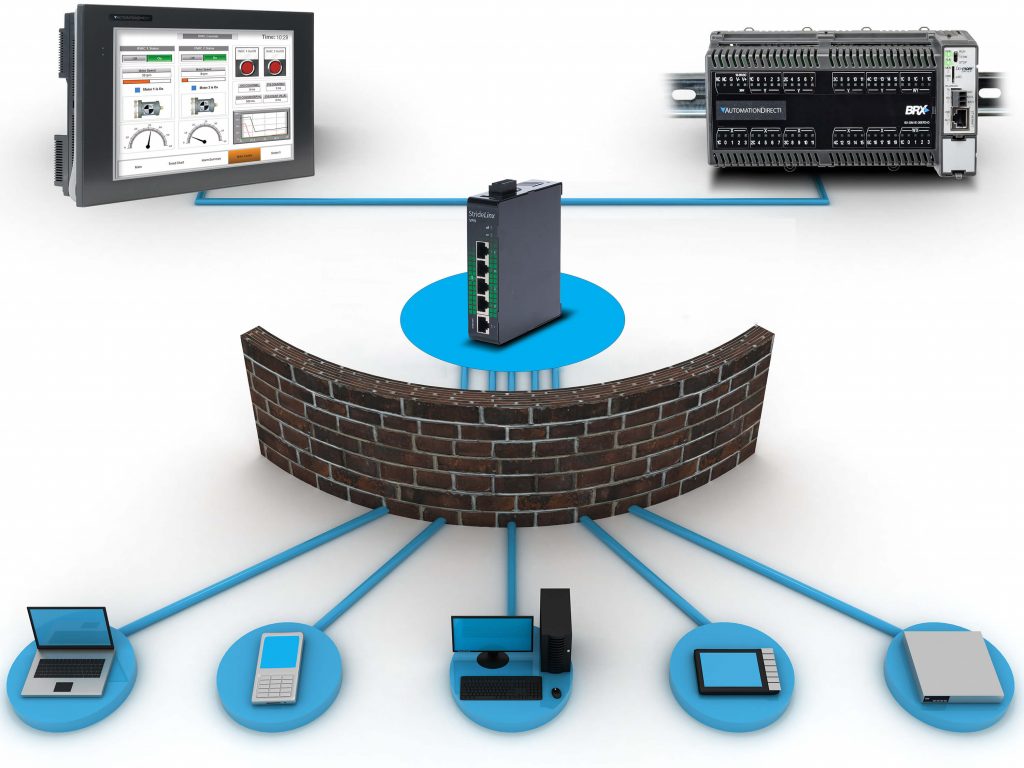
Now that most intelligent automation devices include wired or wireless network connectivity, end users can easily obtain valuable equipment data. However, the more capable PLCs, HMIs, and other devices making this possible also mean that designers need to look for cybersecurity-centric features, and update end user behavior to be focused on such concerns.
Classic Approaches are Not Cybersecure
Many traditional industrial systems have relied on physical “air gaps” or optimistic “security by obscurity,” but the increasing number and sophistication of cyber-attackers means these approaches are not good enough. Bad actors may try to steal data, take over a system, or cause damage and disruption. Fortunately, some PLCs offered today and in the near future will incorporate security features similar to those found in the commercial computing world.

Essential Cybersecurity
Modern PLCs should include the following features to provide cybersecurity and encourage the associated user behavioral changes:
- End-to-end encryption: A processor-intensive capability usually only available in the newest PLCs.
- Username/password protection: Must be built-in, and eventually will be capable of merging with IT-grade cybersecurity.
- Granular access control and port management: Limits access to only known devices, reducing the “attack surface”.
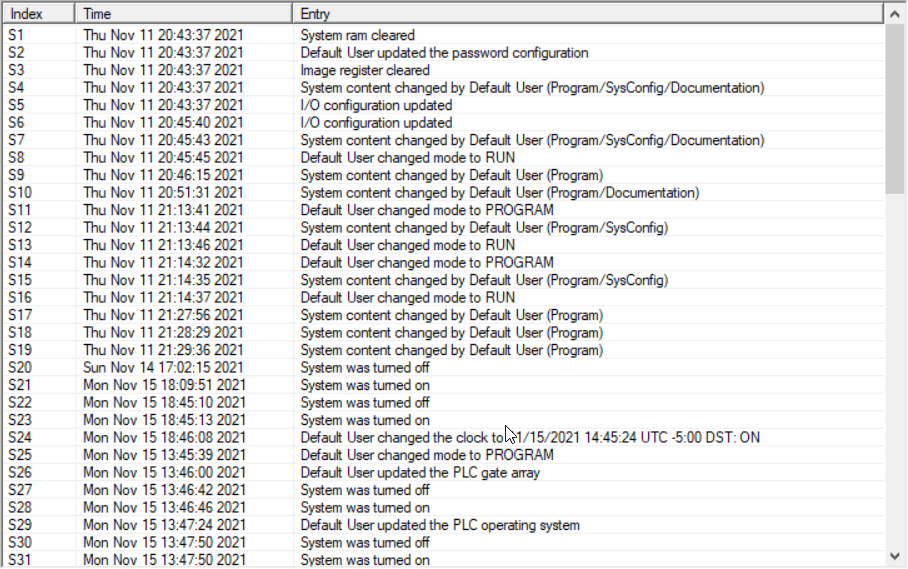
- Activity auditing: Useful for early detection, and after-the-fact investigation.
Secure by Design, Not as an Afterthought
The operating environment today—and continuing into the foreseeable future—will continue to rely on PLCs as the backbone of automation. Legacy models simply don’t have the capability of providing the most effective cybersecurity, so new and retrofit projects call for users to select devices that are secure by design.Fully-integrated cybersecurity should act as infrastructure to seamlessly merge OT with IT, allowing safe data flow from plant floor to the executive floor. Well-designed and secure PLC hardware and software lessens some of the burden on end users while facilitating configuration and management of secure systems.