Industry is certainly starting to take note of the IIoT, which raises cybersecurity issues because it requires connecting field devices and other automation system components to the outside world, often through the internet. Connectivity capability is built into many automation components, typically via an Ethernet port, but can these connections be made secure?

Connections need to follow certain rules, and the IT department of a company should be involved in implementation. If connection to the IIoT is needed, the required infrastructure or service, such as a virtual private network (VPN) or a remotely hosted system, must be in place. A safe and secure connection costs more at the hardware level than a simple, less secure network, and although a great place to start, network security shouldn’t stop there.
Security in Layers
Layered security, or defense in depth as the Department of Homeland Security refers to the concept, is a network defense strategy with multiple security layers to slowdown an attacker. There are many layers including physical access security, authorization and authentication, and data and communications encryption, with new technology layers being added.
Although not discussed here, don’t forget about some of the other defense-in-depth strategies such as providing physical separation between corporate and control networks, employing DMZ zones, disabling unused ports and services, intrusion detection and antivirus software, and management of the upgrades and the remediation of security issues. All of these layers are typically planned out during the single-point failure analysis and the risk mitigation phase of the project, but let’s get back to the physical access security layer.
Restricting physical access starts at the facility fence line, and continues all the way to the control cabinet or server room door. Placing the computers and controllers behind locked doors is a cost-effective way to reduce tampering and theft.
Authorization and Authentication
Another layer of security for IIoT connected networks is authorization and authentication. A variety of access controls are available to authenticate and restrict who has access to what data. Built-in tools are often available, in human machine interfaces (HMIs) and smartphones for example, enabling implementation of username and password policies. Role-based access controls can also be used, for example to keep operators out of engineering or technician functions and screens. Access lists provide security to a network by limiting access to only those users on a certain list. Access lists can also be used to decide which traffic is forwarded and which is blocked.
Authentication should be addressed at the HMI and hand held device level (smartphones and tablets), and with all plant floor PCs. Implementing a basic username and password requirement can restrict unauthorized users from accessing functionality and data in HMIs, databases and other plant floor applications.
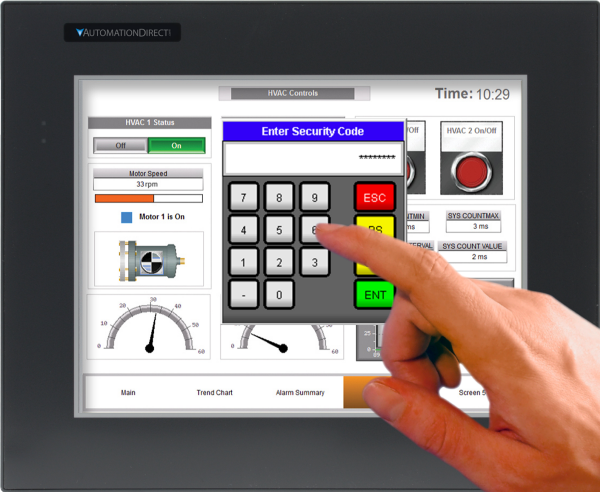
Access control lists and application whitelisting is the next level, limiting access to sensitive data or network areas. Predefined accounts can be created to restrict each user’s level of access to only what’s necessary for him or her to perform their job. These accounts can be configured during the design stages of an HMI application, a task made easier when using modern HMIs with built in security and data encryption.
Network managers are typically responsible for implementing security features per industry standards and company policies. A good place to start is Homeland Security’s National Cyber Security Division, Control Systems Security Program titled, Recommended Practice: Improving Industrial Control Systems Cybersecurity with Defense-In-Depth Strategies.
Remote Access Introduces Issues
Remote access presents security difficulties because information is now flowing into and out of the facility to users worldwide. While physical security and authentication are relatively easy ways to secure sensitive data, remotely accessing devices through a router and firewall is more complicated. This remote access is provided through another level of security which may include port forwarding, IP Security (IPSec) protocols and VPNs—all technologies that take some work to configure.
The port forwarding feature in routers and firewalls allows incoming messages from the IIoT to go to a specific device inside the facility. However, since port forwarding routs data between two devices, often over unknown networks, it opens a port to a hacker, so data could be intercepted and possibly changed.
The IPSec protocol closes up the port by providing authentication of the sender, and data encryption. It can be implemented at the end host or in routers. It’s also useful for implementing VPNs for remote access to private networks.
A VPN is a reliable way to secure a remote access connection from a public network. It makes the remote device appear to be on the local network by giving the device an IP address on the network. This provides a secure remote access connection. However, these connections can be difficult to configure.
See the cellular remote access blog here.
Easy to Secure Layers
Security requirements don’t change whether working locally or remotely. Fortunately, new technologies are making it easier to exchange data using the IIoT. There are several plug-and-play firewalls that are industrial protocol-aware, and many cloud providers provide excellent network security capability.
With the development of more powerful field devices, the weakest links are still authentication, authorization and secure communications. Some of the emerging technologies addressing these weaknesses include cloud access security broker (CASB) and software-defined networking (SDN)
CASB is middleware installed between a cloud service and a cloud user such as a smartphone, HMI or PC. To help secure internet and cloud-based applications, CASB manages and enforces enterprise security policies. Although CASB is not here yet, it’s coming in the form of cybersecurity-as-a-service. This will make it easier to secure network communication with a diverse set of cloud providers connected to the local network.
Another new technology simplifying network security is SDN. SDN is similar to server, HMI and PC workstation virtualization. In SDN’s case, it separates network configuration and security policy from the physical hardware and connections. The ability to create hardware instances virtually using software makes dynamic changes to network resources possible. Changes, expansion and reconfiguration become much quicker when network traffic and security are separated from the network hardware.
There are many more layers and new technologies to consider, as well as new security threats which will emerge. While one or two layers may eliminate most security threats, adding more layers will help eliminate them all.