Let’s face it, we are living in the age of the hacker and in the cat-and-mouse game of cyber warfare, hackers have racked up some pretty impressive scores. From the most recent WannaCry attack, to exposing Ashley Madison, to reportedly “stealing an election”, hackers have been busy exploiting vulnerabilities and gaining massive notoriety. A recent study by the Identity Theft Resource Center concluded that in 2016 U.S companies and government agencies were breached 1,093 times. That’s a new record and a 40% increase from the 780 breaches in 2015. But it’s not the number of attacks, instead it’s the size of the score and the resulting damage that’s so striking. In the 2014 Home Depot data breach, hackers were able to compromise store self-check-out terminals and steal email and credit card information from more than 50 million customers. Fifty million! It is estimated that this one attack will cost Home Depot at least $179 million in restitution, with some estimates much higher when legal fees and undisclosed payouts are accounted for. The Home Depot breach was one of many wake-up calls for the corporate world, but unfortunately some of the biggest government agencies were also asleep. The 2015 IRS data breach, where hackers infiltrated the Internal Revenue Service’s “Get Transcript” system and gained access to over 700,000 accounts which contained sensitive financial information and Social Security numbers, is believed to have cost taxpayers $50 million in bogus claims.
 There’s no way around it, hacking has become a very profitable business. That’s why hackers are so persistent and why they are constantly improving their methods. Methods that range from simple phishing emails, which trick victims into providing personal information through a fraudulent email (phishing scams account for about 56 percent of all breaches last year according to the Identity Theft Resource Center), to Denial of Service (DOS) attacks, which attempt to overload a website with traffic causing a crash, to cookie theft. And while you are probably familiar with phishing since we all seem to have distant relatives in Nigeria who left us an inheritance, or like me, your PayPal account has a problem and is about to be frozen, hackers are constantly looking for new avenues and techniques that you are unaware of. Some of these techniques can even originate from unexpected places as was seen with the recent WannaCry ransomware attack.
There’s no way around it, hacking has become a very profitable business. That’s why hackers are so persistent and why they are constantly improving their methods. Methods that range from simple phishing emails, which trick victims into providing personal information through a fraudulent email (phishing scams account for about 56 percent of all breaches last year according to the Identity Theft Resource Center), to Denial of Service (DOS) attacks, which attempt to overload a website with traffic causing a crash, to cookie theft. And while you are probably familiar with phishing since we all seem to have distant relatives in Nigeria who left us an inheritance, or like me, your PayPal account has a problem and is about to be frozen, hackers are constantly looking for new avenues and techniques that you are unaware of. Some of these techniques can even originate from unexpected places as was seen with the recent WannaCry ransomware attack.
WannaCry
This attack was made possible by a data breach at the National Security Agency (NSA). The NSA had recently discovered a vulnerability in the Windows® operating system that would provide an undetected “window” (pun intended) into computer systems worldwide. Instead of reporting the vulnerability, they filed it away as a means for future intelligence gathering. Unfortunately, a group of hackers, known as Shadow Brokers, stole a host of NSA documents and released them on the internet. These documents contained details about the Windows vulnerability which led to the creation of WannaCry, believed to have originated from North Korea. So far, WannaCry has compromised more than 200,000 computers in 150 countries around the globe, locking people and corporations out of their data and demanding a ransom to regain access.
What about PLCs?
Hackers, especially state-sponsored ones, are extremely active and are becoming more brazen, well-funded, and capable of pulling off even more sophisticated attacks. State-sponsored hackers aren’t solely focused on the profits that organized crime hackers seek, with possible targets including a rival country’s infrastructure or economy. A country’s power grid, water treatment facilities, military systems or nuclear sites are some of the possible targets for these rogue states. Regrettably, one technique that can be used to facilitate these attacks has already been highly publicized and yes, it involved PLCs.
The Stuxnet virus, believed to be a joint venture between Washington D.C. and Tel Aviv, was used to attack Siemens PLCs at the Iranian nuclear plant in Natanz. The virus was believed to have entered the nuclear facility on a thumb drive. Once inside, Stuxnet compromised the facility’s PLCs, collecting information and causing fast-spinning centrifuges to spin out of control and destroy themselves. Reportedly, Stuxnet ruined almost 20% of Iran’s nuclear centrifuges. Although the Stuxnet attack was used ostensibly to deal a critical blow to the nuclear capabilities of a worrisome government, the attack consequently provided new avenues for those who wish to replicate such destruction.
A study conducted on the Stuxnet virus by the SAP research group in Germany concluded that Stuxnet successfully proved to the masses that a very targeted and highly sophisticated cyberwarfare attack was possible. The study also found that Stuxnet’s design and architecture are not domain-specific and with some modifications could be tailored as a platform for attacking other automated systems e.g. automobile or power plants.
PLCs with added security
For many years, the industrial sector was isolated from the outside world, foregoing open communication for in-house proprietary means. This type of communication provided a level of inherent security from prying eyes and those wishing to do harm. But with the recent acceptance and explosion of Ethernet in the industrial world and with the current drive to connect as many “things” as possible through Ethernet and the Industrial Internet of Things (IIoT), industry is more vulnerable than ever. It’s imperative in today’s connected world that industrial facilities guard their automated systems from possible cyber attacks. Using firewalls, backing up and encrypting data, keeping firmware/software updated, using antivirus software where possible are all ways to protect your facility from attack. But what about the PLC itself? Newer PLCs, like the Do-more! BRX, have multiple security measures built in to help guard against unwanted intrusion.

Guest Memory
The Do-more! BRX PLC platform reserves a group of internal memory blocks specifically for external communication. These blocks are isolated to prevent external devices (operator panels, HMIs, etc.) from being able to directly control the PLC’s I/O and memory. This method of communication secures the native memory from unwanted access through communication channels.
In practice, when operating as a Modbus server using either Modbus/TCP or Modbus/RTU, the Do-more! BRX PLC routes all Modbus read and write requests from external devices to the four isolated memory blocks that are reserved for external communication. The information stored in this guest memory is available to any ladder logic instruction and can be accessed in place by these instructions. When operating as a Modbus client, the MRX (Modbus Network Read) and MWX (Modbus Network Write) instructions can access all of the native memory as well as the guest memory for any outgoing message data.
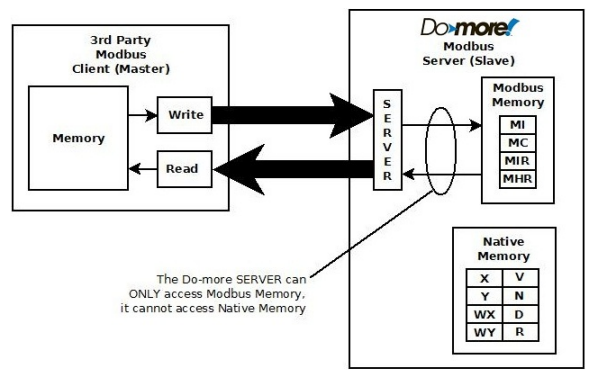
External read/write using guest memory for Server applications
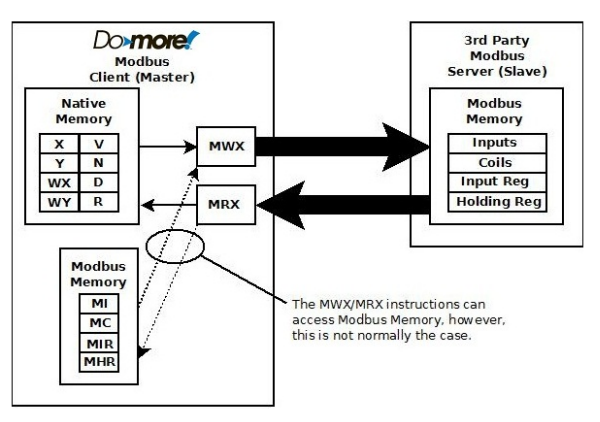
External read/write using ladder instructions for Client applications
Session-based Communication
Many Do-more! BRX controllers will be installed on networks that have varying degrees of isolation. This can cause security concerns for programmers and OEMs who need to have communication with the controller be restricted to authorized personnel only. To this end, the Do-more Designer programming software uses communication sessions any time that the software is online with the controller.
When communication sessions are established, they are done so with a unique ID, and all communication packets must contain that ID. Any packets received without that ID are discarded by the controller. This prevents unauthorized access of the controller, and also prevents other computers on the network from accidentally accessing the wrong controller. A timeout system is also utilized and will terminate a session after a period of time with no communication between the programming software and the controller. The session must be re-established before communication can continue.
Write Protect the Operating System
The BRX PLC includes a block of 8 on-board DIP switches that are used to perform various debug and recovery operations. One of these switches enables/disables firmware downloads to the controller. Disabling firmware downloads will protect your CPU from unwanted operating system changes and keep you in control if and when these changes are made.

Passwords/User Accounts
System security is more than simply allowing or denying the ability to connect to a Do-more! BRX controller based on a user ID and password. System security also involves the creation of accounts that will allow or deny access to the different resources in the controller. By creating multiple accounts, each with different levels of access, you can efficiently limit who has access to the controller and what each of those users can and cannot do. With user accounts, you can also track the operations performed by each account. The Event Log messages will record the active user account for each event that is logged so you know exactly who had access and when.
Advances in industrial communication have provided numerous improvements including faster responses and wider access. However, these advances have also opened up the industrial sector to increasingly active hackers and their growing arsenal of cyber threats. Because of this, it is very important to guard who has physical and online access to your system and its controls. There are many ways to keep your facilities and networks safe and some PLCs, including the Do-more! BRX, offer built-in security measures to help fend off those with bad intentions.
If you would like more information on the BRX controller, please visit www.BRXPLC.com
For more information about programmable control, click here.
Originally Published: May 2017